| This topic discusses these procedures: | Links to related topics: |
| Main Help Page | Search Online Doc | Shortcut Keys |
This topic outlines security for ERP iPad applications. The discussion is oriented to system administrators at sites that have the ERP mobile applications enabled.
Security is provided in several areas for users of the iPad applications:
A role specifies task and ERP feature areas -- called role objects -- that users assigned to the role may work with. For example, the DistributionClerk role includes the role objects Distribution (picking/issuing) and Receiving, among others. Each role object has a value -- such as create, modify, view, none, and all -- that determines the level of access allowed to the user.
A detailed discussion of roles and role objects is in the topic "Set Up and Maintain Users."
Table 1 lists role objects and their values needed for mobile applications users.
| Role Object | Purpose | Minimum Required Setting |
| Distribution | Allows picking and issuing. Controls access to the Picks button on the mobile application. Note: The mobile Picks feature must be enabled for your site by the Help Desk. |
Create |
| Mobile Price Check | Allows mobile users to do price checks. Controls access to the Price Lookup button on the mobile application. Note: The mobile Price Check feature must be enabled for your site by the Help Desk. |
View |
| Mobile Admin | For system administrators: Allows administering user settings for mobile applications on the server side (i.e., within ERP running on the server). | Create |
Access permissions control an iPad user's ability to get data from the ERP server, and the organization/department data that the user can work with.
The fields for granting access are available from the "Work in Administration" Users list: Work in Administration > Administration > Users.

A panel appears with options to select for the mobile user (Figure 2).
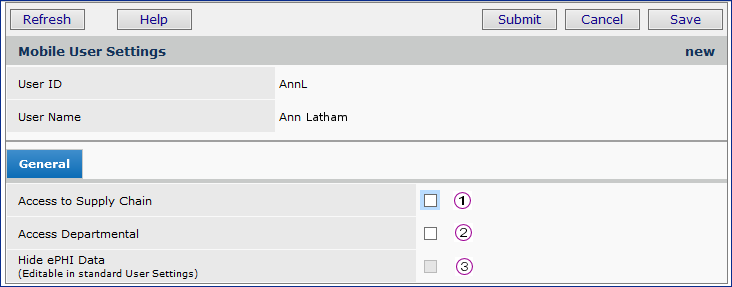
![]() Access to Supply Chain gives the mobile user access to applications that interface with ERP data that resides on the server (e.g., order guides, par carts, picks, etc.).
Select this field. (Unselected, the user cannot access sub-level applications: the iPad Supply Chain button does not appear.)
Access to Supply Chain gives the mobile user access to applications that interface with ERP data that resides on the server (e.g., order guides, par carts, picks, etc.).
Select this field. (Unselected, the user cannot access sub-level applications: the iPad Supply Chain button does not appear.)
![]() Access to Departmental restricts the user to working with applications that have been designated as departmental, as opposed to warehouse responsibilities (e.g., order guide management).
Access to Departmental restricts the user to working with applications that have been designated as departmental, as opposed to warehouse responsibilities (e.g., order guide management).
![]() Hide ePHI Data (not selectable on this panel) repeats the setting on the user profile General tab for access to ePHI information. In Figure 2, the user can view ePHI data, since the field was not checked on the General tab.
Hide ePHI Data (not selectable on this panel) repeats the setting on the user profile General tab for access to ePHI information. In Figure 2, the user can view ePHI data, since the field was not checked on the General tab.
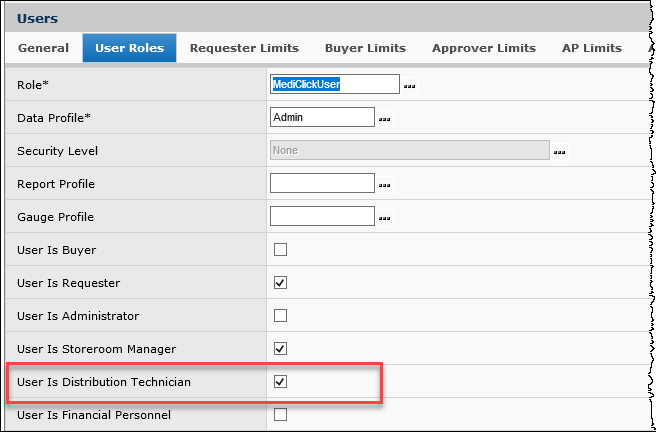
Users who work with mobile applications must have the role "User is Distribution Technician" selected on the User Profile Roles panel.
Other user profile options control whether mobile application users can issue items or return items to inventory, and whether users can adjust inventory quantities during a pick (Figure 4).
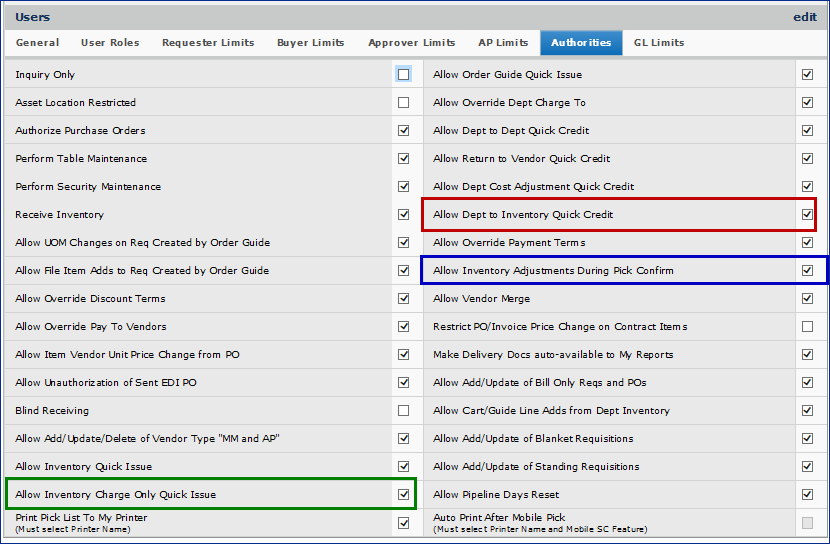
Note: Also, on the User Profile General tab, be sure to set the field for ePHI (electronic personal health information) correctly for the user. This field is Hide ePHI Data. See the online topic "Securing Electronic Protected Health Information" for a discussion of this field.
Each user at your site is assigned a data profile. A data profile contains the regions, organizations, departments, and asset locations whose data the user can work with. System administrators can define data profiles and assign them to users.
The mobile user's data profile specifies the departments and supplying organizations and asset locations that the user can access. The par carts (and par groups) allowed for the mobile user are thus controlled by the user's data profile settings. Similarly, the data profile settings control the order guides that the user can fill requisitions from.
To perform an item count during a physical inventory, the user must have data profile access to the organization and asset location for the inventory.
Some sites have mobile users share iPads for work with the ERP mobile applications.
- When a user is working with an iPad application and locks it from a working panel (not from the table of contents), another user can only unlock it when his/her permission levels are the same as the first user.
- Otherwise, the first user will need to unlock the application at the panel last used, return to the table of contents, and then lock the application again. The second user can then log in and have access at his/her own permission level.
Copyright © 2023 by Premier Inc. All rights reserved.